Adguard
AdGuard Home functions as a DNS sinkhole, blocking connection requests to domains or hosts identified as ad servers and trackers, while also providing built-in support for DNS over HTTPS (DoH) to enhance privacy. Unlike Pi-Hole, which requires extra setup, AdGuard Home simplifies this process. With its DoH capabilities, it enables convenient use on mobile devices without necessitating a VPN, and it offers the flexibility to create whitelists in addition to blocklists.
Prerequisites
- Docker Engine and Docker Compose packages are installed and running
- A non-root user with Docker privileges
Setting up the adguard Server
Create the directory structure
To keep the docker directory clean i have created a adguard directory to store the configuration file. My file structure is as follows:
1
2
mkdir ~/docker/adguard/{conf,work}
touch ~/docker/adguard/docker-compose.yml
1
2
3
4
5
6
7
8
9
10
11
📂adguard
|-- 📂conf
| `-- 📑 AdGuardHome.yaml
|-- 📂work
| `--📂data
|-- filters
| `-- 1.txt
|-- querylog.json
|-- sessions.db
`-- stats.db
|-- 📑docker-compose.yml
Docker Configuration
As we have created the docker compose file lets edit the files with your favorite editors of choice
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
---
version: "3"
services:
adguardhome:
image: adguard/adguardhome
container_name: adguardhome
environment:
- PUID=1000
- PGID=1000
volumes:
- ./conf:/opt/adguardhome/conf
- ./work:/opt/adguardhome/work
ports:
# DNS
- 53:53
# # DHCP server
# - 67:67/udp
# - 68:68/tcp
# - 68:68/udp
# # HTTPS/DNS-over-HTTPS
# - 443:443/tcp
# # DNS-over-TLS
# - 853:853/tcp
# # DNS-over-QUIC
# - 784:784/udp
# # DNSCrypt
# - 5443:5443/tcp
# - 5443:5443/udp
# # WebUI
- 3000:3000/tcp
restart: unless-stopped
networks:
routevlan:
ipv4_address: 192.168.1.100
proxy:
networks:
routevlan:
external: true
proxy:
external: true
#routevlan:
# name: routevlan
# driver: macvlan
# driver_opts:
# parent: eth1 # using ifconfig
# ipam:
# config:
# - subnet: "192.168.1.0/24"
# ip_range: "192.168.1.100/32"
# gateway: "192.168.1.1"
As the Adguard service is relays on the network to block the adds on the network i recommend you to use the docker macvlan. AdGuard Home Docker service would act as a separate machine thereby eliminating any port conflicts.
Verify and launch the container
to verify the docker compose files has no issues use docker compose config Once you have the docker-compose.yml file you can run docker-compose up -d which will create the volume, download the image and start the container in the background
To verify the status of all running containers, run the docker-compose command:
1
docker-compose ps (OR) docker ps -a
If something goes wrong, you can check the logs for each container using the docker logs command and specify the service name. For example, to check the log of the Nginx Proxy Manager container, run the following command:
1
docker logs $container (OR) docker compose logs -f
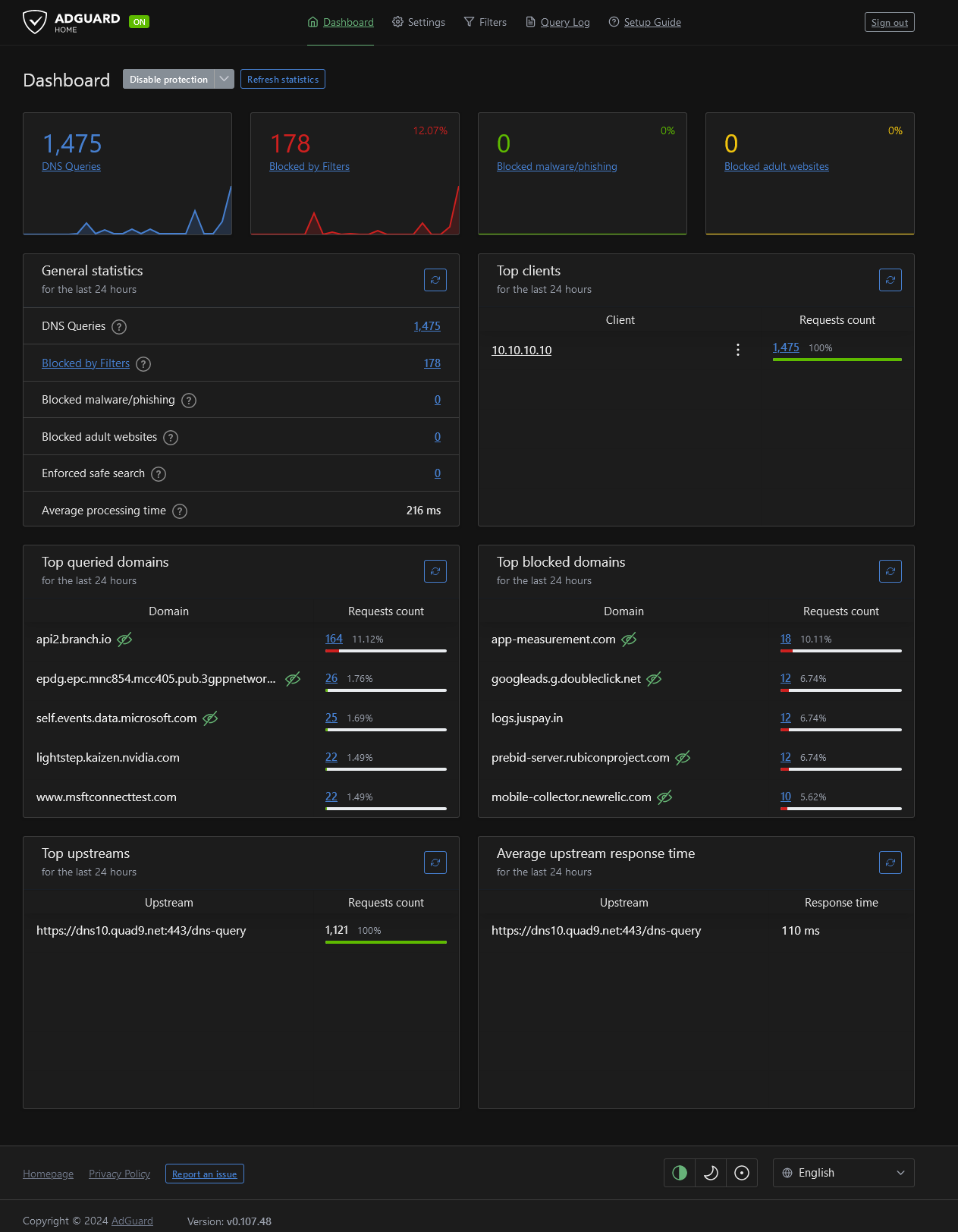
Accessing the Adguard dashboard
If all is well, you can locally view your adguard Server by navigating to http://localhost:PORT. Or from another machine by using your ip (macvlan ip) address.
You should see something that looks like the following.
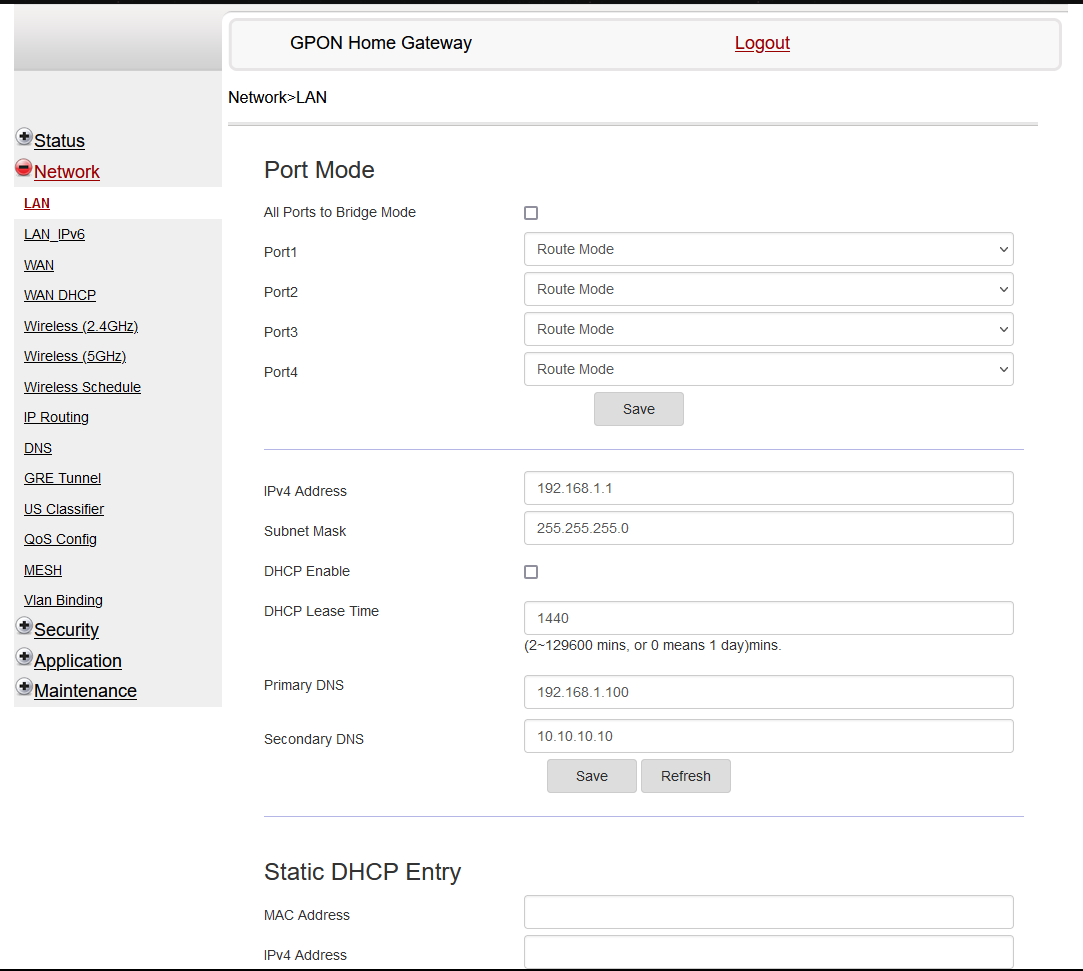
Setup DNS service on router
To use AdGuard Home, replace the default DNS server IPs with your AdGuard Home IP address (macvlan ip) in your router or other devices. If you haven’t altered DNS settings before, typically there won’t be any IP address configured in your settings. DNS configuration depends on the routers you use please google them according.
If you like you can use the adguard default DHCP service for assigning the IP address in your network instead of the default router DHCP.